Quantum Computing Breakthroughs in 2025: Impact on AI and Encryption Security
Table of Contents
1. Introduction: Quantum Computing’s New Era and Its Dual Impact on AI and Encryption
Quantum computing has rapidly transitioned from theoretical physics labs to tangible breakthroughs that promise to redefine the landscape of technology in 2025. Unlike classical computers that use bits as the smallest unit of data, quantum computers leverage qubits capable of representing both 0 and 1 simultaneously through quantum superposition. This exponential increase in processing power has profound implications—particularly for fields like artificial intelligence (AI) and encryption.
On one hand, quantum computing accelerates AI’s ability to process vast datasets and solve complex optimization problems, opening new frontiers in machine learning, natural language processing, and autonomous systems. On the other hand, it threatens current cryptographic systems that underpin digital security by making traditional encryption algorithms vulnerable to quantum attacks.
Understanding these dual impacts is crucial for developers, cybersecurity professionals, and business leaders aiming to harness the benefits of quantum advancements while preparing for emerging risks. This blog will explore recent breakthroughs in quantum computing and decode what they mean for the future of AI and encryption security.

2. How Quantum Computing Accelerates Artificial Intelligence
Quantum computing’s unique ability to process and analyze information at an exponential scale offers groundbreaking opportunities to advance artificial intelligence. Traditional AI algorithms often rely on classical computing architectures that, despite their power, face limitations when tackling highly complex problems involving massive datasets or intricate pattern recognition.
Quantum algorithms, such as Grover’s search and quantum annealing, can dramatically speed up optimization, training, and data processing tasks critical to AI development. For instance, quantum-enhanced machine learning models can explore larger solution spaces more efficiently, leading to faster training times and improved accuracy in applications like image recognition, natural language understanding, and drug discovery.
Moreover, quantum AI holds promise for developing new types of neural networks that leverage quantum phenomena like entanglement and superposition to perform computations beyond the scope of classical networks. These quantum neural networks could unlock levels of reasoning and decision-making currently unattainable, potentially transforming industries from healthcare to finance.
However, integrating quantum computing with AI also presents challenges, including the current hardware limitations, error rates in qubits, and the need for novel quantum algorithms tailored specifically for AI tasks. Despite these hurdles, ongoing research and prototype quantum processors signal a future where AI powered by quantum computing becomes a game changer.
3. Quantum Computing’s Threat to Traditional Encryption Systems
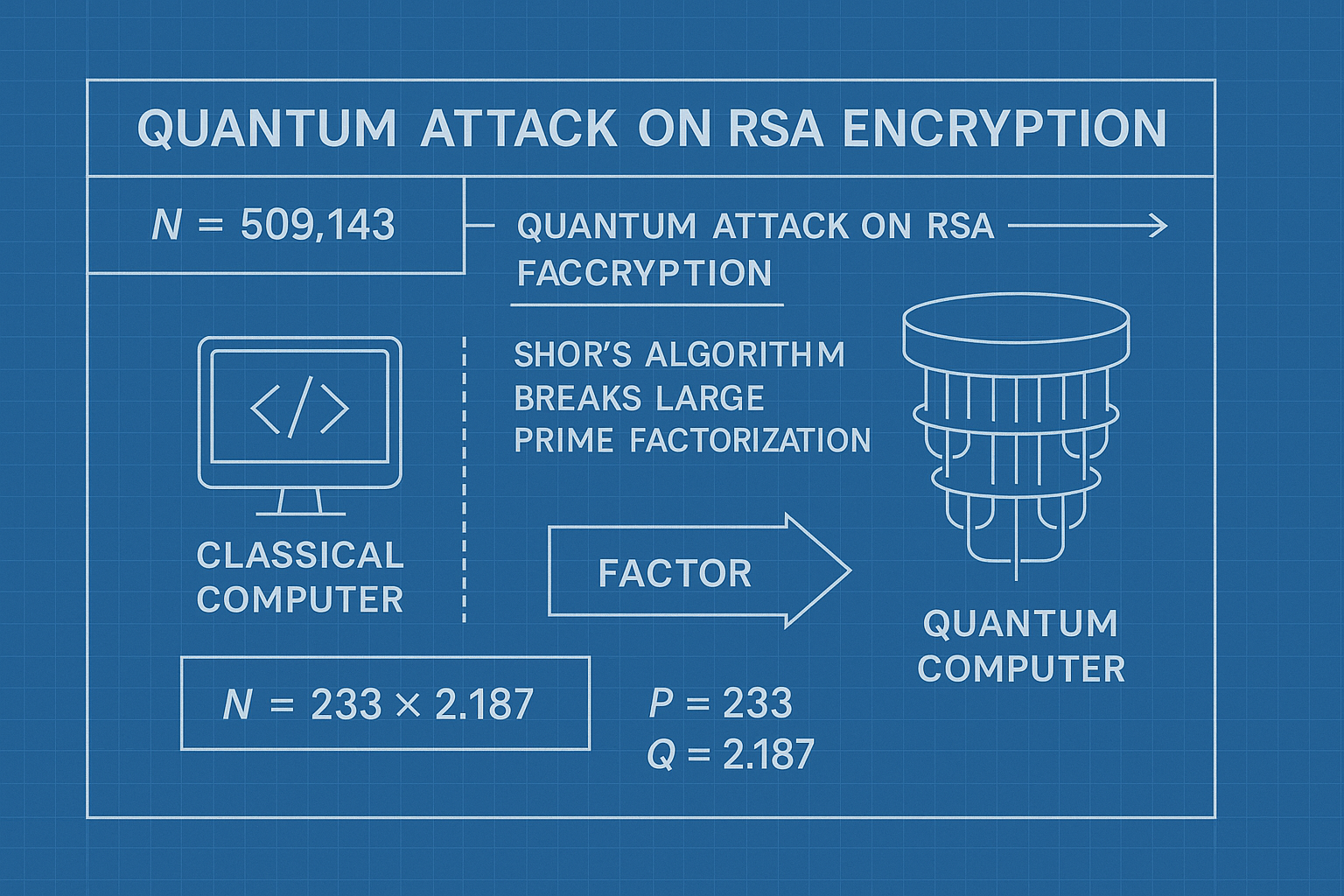
Quantum computing’s unparalleled processing power also brings a looming threat to the encryption methods that safeguard our digital world today. Most modern cryptographic systems, including RSA (Rivest–Shamir–Adleman), ECC (Elliptic Curve Cryptography), and symmetric key algorithms like AES (Advanced Encryption Standard), rely on mathematical problems that are computationally infeasible for classical computers to solve in a reasonable time.
However, quantum algorithms such as Shor’s algorithm have the potential to solve these problems exponentially faster. Shor’s algorithm can efficiently factor large integers and compute discrete logarithms—tasks that underpin the security of RSA and ECC—rendering them vulnerable to being broken by sufficiently powerful quantum computers.
This threat puts at risk everything from secure online communications, banking transactions, encrypted emails, to digital signatures and blockchain technologies. As quantum hardware advances, organizations face increasing pressure to transition to post-quantum cryptography—new encryption methods designed to be resistant to quantum attacks.
Post-quantum cryptography includes lattice-based cryptography, hash-based signatures, code-based cryptography, and multivariate polynomial cryptography. While still under standardization and evaluation by bodies like NIST (National Institute of Standards and Technology), these quantum-safe algorithms aim to secure data against future quantum adversaries.
Preparing for a quantum-safe future involves a proactive approach: auditing existing cryptographic systems, investing in research, and gradually migrating to hybrid models that combine classical and quantum-resistant algorithms.
Unlock exclusive, detailed insights with our free downloadable PDF—your ultimate companion to mastering this topic.
4. Post-Quantum Cryptography: Securing Data in the Quantum Era
As the quantum threat to classical encryption becomes more imminent, the field of post-quantum cryptography (PQC) has gained critical importance. PQC focuses on developing cryptographic algorithms that can withstand attacks from both classical and quantum computers, ensuring long-term security for sensitive data.
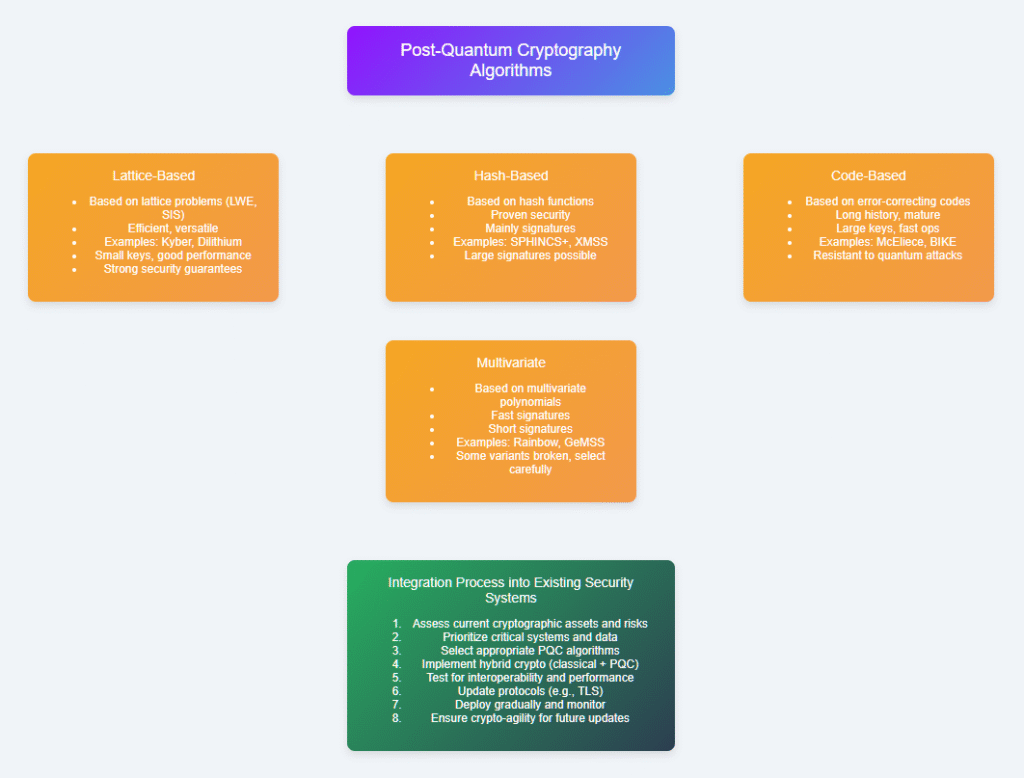
Several promising PQC approaches are currently under evaluation and standardization by organizations like NIST. These include:
- Lattice-Based Cryptography: Utilizes complex mathematical structures called lattices, offering strong resistance against quantum attacks and efficient performance. Examples include Learning With Errors (LWE) and Ring Learning With Errors (RLWE) schemes.
- Hash-Based Signatures: Rely on the security of cryptographic hash functions to create digital signatures that quantum computers cannot easily forge. They are well-studied but often produce larger signatures.
- Code-Based Cryptography: Based on error-correcting codes, this approach has a strong security foundation but may require larger key sizes.
- Multivariate Polynomial Cryptography: Uses systems of multivariate equations that are difficult for quantum algorithms to solve efficiently.
Transitioning to PQC poses challenges, such as increased computational overhead, larger key sizes, and integration complexities with existing systems. However, hybrid cryptographic solutions that combine classical and quantum-resistant algorithms during the transition period are a practical approach currently adopted by many organizations.
Governments and industries are investing heavily in PQC research to prepare for a seamless migration and to protect critical infrastructure, financial systems, and personal data from future quantum decryption threats.
5. The Intersection of Quantum Computing and Cybersecurity: Risks and Opportunities
Quantum computing’s impact on cybersecurity is twofold: while it threatens to undermine current encryption methods, it also offers innovative tools to strengthen defenses against cyber threats.
Risks:
As discussed, quantum computers could enable attackers to break widely used encryption, compromising secure communications, financial transactions, and confidential data. This risk is especially critical for data requiring long-term confidentiality, such as government secrets or personal medical records. The window of vulnerability grows as quantum hardware improves, raising urgency for immediate defensive measures.
Opportunities:
Conversely, quantum technologies can enhance cybersecurity. Quantum key distribution (QKD) is a cutting-edge technique that uses principles of quantum mechanics to enable theoretically unbreakable encryption keys, ensuring secure data transmission even in the presence of eavesdroppers. QKD systems are already being piloted in secure communication networks worldwide.
Moreover, quantum-enhanced algorithms can improve malware detection, threat analysis, and anomaly detection by processing massive datasets faster and recognizing complex patterns beyond classical capabilities. This could lead to more proactive, adaptive cybersecurity defenses.
The convergence of quantum computing with AI-driven security tools opens a promising frontier, enabling intelligent and resilient protection mechanisms to counteract evolving cyber threats.

6. Preparing for the Quantum Future: Industry and Regulatory Responses
Recognizing both the promise and risks of quantum computing, governments, industry leaders, and standardization bodies are mobilizing to create frameworks and strategies to navigate the quantum era safely and effectively.
Industry Initiatives:
Major tech companies and cybersecurity firms are investing heavily in quantum research and developing quantum-resistant security products. Many are adopting hybrid cryptography models that blend classical and post-quantum algorithms to ensure secure transitions. Collaboration across sectors is fostering innovation in hardware, software, and security protocols designed for quantum resilience.
Regulatory Efforts:
Government agencies worldwide, including NIST in the U.S., the European Union’s ENISA, and others, are actively working to establish quantum security standards and guidelines. These regulations focus on mandating quantum-safe cryptographic standards, encouraging secure AI development, and promoting transparency around quantum risk management.
Workforce Development:
Building a skilled workforce equipped with quantum computing and cybersecurity expertise is a priority. Educational institutions and professional organizations are expanding quantum-focused curricula and certifications to prepare developers, security analysts, and policymakers for the emerging challenges.
Global Cooperation:
Since quantum threats transcend borders, international cooperation is critical. Information sharing, joint research projects, and unified policy frameworks help create a coordinated global defense against quantum-enabled cyber threats.

7. Practical Steps for Developers and Organizations to Prepare for Quantum Impact
While fully scalable quantum computers are still emerging, developers and organizations can start preparing today to mitigate risks and leverage opportunities presented by quantum computing:
- Audit Current Cryptography:
Review and inventory existing cryptographic systems, identify those vulnerable to quantum attacks, and plan migration strategies. - Adopt Hybrid Cryptographic Solutions:
Implement hybrid encryption methods combining classical and post-quantum algorithms to ensure security during the transition phase. - Invest in Quantum-Safe Research:
Support and follow developments in post-quantum cryptography, participate in standardization efforts, and experiment with PQC libraries and tools. - Enhance AI Integration:
Explore quantum-enhanced AI tools for cybersecurity, focusing on anomaly detection, threat prediction, and automated response capabilities. - Train and Upskill Staff:
Provide training programs on quantum computing fundamentals, cryptography, and cybersecurity best practices to keep teams prepared. - Engage with Industry Consortia:
Collaborate with security communities, standard bodies, and vendors to stay updated on quantum-safe technologies and share threat intelligence. - Monitor Regulatory Developments:
Keep abreast of evolving laws and compliance requirements related to quantum security and data protection.
By proactively adopting these steps, organizations can build resilience against future quantum threats while positioning themselves to harness the transformative power of quantum computing.
8. Conclusion: Embracing Quantum Computing with Caution and Vision
Quantum computing is set to revolutionize both artificial intelligence and encryption, unlocking unprecedented computational capabilities while simultaneously challenging the security foundations of our digital world. The breakthroughs in quantum technology offer exciting possibilities for advancing AI, enabling smarter, faster, and more complex systems. However, they also compel us to rethink and redesign cryptographic standards to defend against quantum-enabled cyber threats.
Navigating this dual-edged frontier requires a balanced approach—embracing innovation with caution. Developers, organizations, and policymakers must work together to accelerate the adoption of post-quantum cryptography, invest in quantum-safe AI tools, and foster global cooperation on regulation and standards.
By proactively preparing today, we can harness the transformative power of quantum computing responsibly, ensuring that the digital infrastructure of tomorrow remains secure, trustworthy, and capable of supporting the next generation of intelligent technologies.
Stay informed, stay agile, and stay secure in the quantum era.
FAQS
Q1: What makes quantum computing different from classical computing?
A: Quantum computing uses qubits that can exist in multiple states simultaneously thanks to superposition, allowing it to process complex calculations exponentially faster than classical bits that are either 0 or 1.
Q2: How does quantum computing threaten current encryption methods?
A: Quantum algorithms like Shor’s algorithm can efficiently break widely used encryption schemes such as RSA and ECC by factoring large numbers and solving discrete logarithms much faster than classical computers.
Q3: What is post-quantum cryptography?
A: Post-quantum cryptography refers to cryptographic algorithms designed to be secure against attacks from quantum computers, including lattice-based, hash-based, and code-based cryptographic methods.
Q4: Can quantum computing improve artificial intelligence?
A: Yes, quantum computing can accelerate AI by speeding up data processing, optimization, and enabling new quantum neural network architectures, potentially transforming machine learning and decision-making capabilities.
Q5: How can organizations prepare for the impact of quantum computing?
A: Organizations can prepare by auditing current cryptographic systems, adopting hybrid encryption solutions, investing in quantum-safe research, training staff, and staying informed on regulatory developments and industry best practices.
